Table of Contents
Does SSL-Labs test for HTTPS assessing your site as ‘B’ grade? Is it complaining that your server still supports TLSv1.0 (Transport Layer Security protocol) and TLSv1.1? To know how to enforce a minimum TLSv1.2 version on your Nginx server, read on:
Before Configuration
The following screenshot shows a sample test result from SSL-Labs where it tests a website’s SSL certificate and configuration.
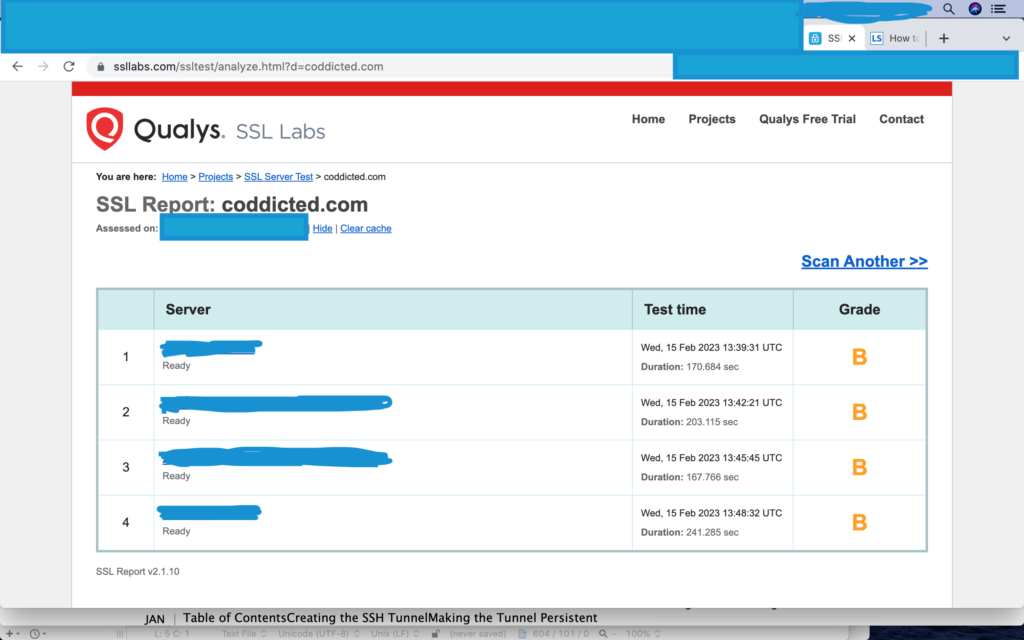
As seen above, the test give a ‘B’ grade to the site, which on investigation seems to have complaint about the server still supporting older versions of TLS, viz. TLSv1.0 and TLSv1.1
Configure TLSv1.2 on your Nginx
If you’re using Nginx as your reverse-proxy/ HTTPS termination server, then following configuration change is needed in order to enforce TLSv1.2 (or v1.3 as per your interest) for all traffic:
Edit the Nginx config files
We’ll edit following two files:
- /etc/nginx/nginx.conf
- /etc/nginx/sites-available/example.com (or /default)
Edit nginx.conf file
First backup the file as precautionary measure:
|
1 |
sudo cp /etc/nginx/nginx.conf /etc/nginx/nginx.conf.backup |
In order to edit, open with say vi editor:
|
1 |
sudo vi /etc/nginx/nginx.conf |
locate the http { } block and within this block the line starting with ssl_protocols. Edit the line to read like below:
|
1 |
ssl_protocols TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE |
the text after # is just a comment. Don’t worry if it’s not there already
test if nginx configuration is valid
|
1 |
nginx -t |
Reload/ restart nginx
|
1 |
sudo service nginx reload |
Edit server block configuration file
Find your server configuration file:
|
1 2 |
cd /etc/nginx/sites-available/ ls -l |
Edit the server block configuration, for example:
|
1 2 3 |
sudo vi /etc/nginx/sites-available/default OR sudo vi /etc/nginx/sites-available/example.com |
Again, look for the following line:
|
1 |
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; |
Edit the above line, if present, or else add the below line in your server { } configuration block (for port 443)
|
1 2 3 4 5 |
ssl_protocols TLSv1.2 TLSv1.3; ssl_prefer_server_ciphers on; ssl_ciphers "ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS"; |
Read more about ssl_prefer_server_ciphers option here.
Save and exit the file, test and reload nginx configuration as in previous step.
|
1 2 |
nginx -t sudo service nginx reload |
Update Cloudflare SSL/ TLS configuration for minimum TLS version
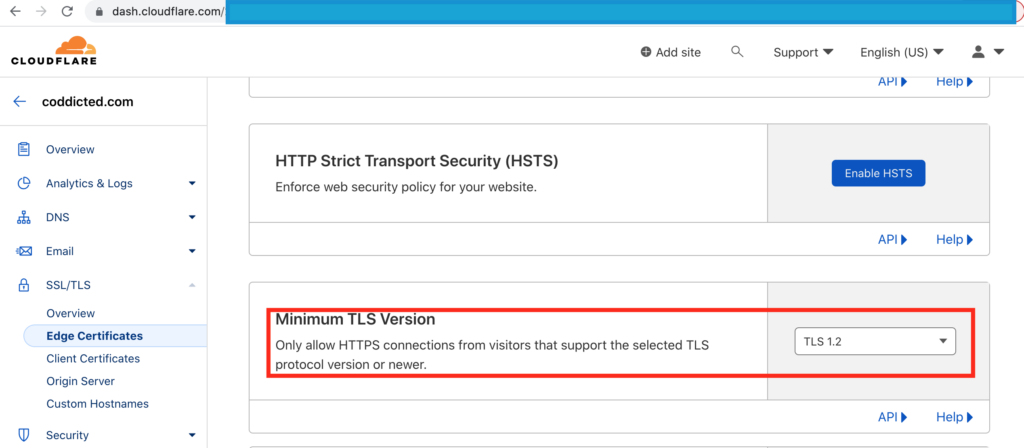
If your domain registry is on Cloudflare, there’s a chance that it’s still allowing TLS versions below 1.2. To check and update please see the screen below.
Under SSL/TLS section for your site, locate Edge Certificates and within the page, locate Minimum TLS Version section. Update the drop-down for minimum TLS version to TLS 1.2 (highlighted in red box). Once new value is selected, the configuration is automatically saved and applied to your site configuration.
For other domain registrars, please consult/ search over web for corresponding minimum TLS version settings.
Why the hassle?
At this point, you might be wondering what happens if above settings are not done or why specify all those ciphers list? After all, the website is already running on HTTPS and my browser does not seem to complain about anything?
Well the answer is to keep control of encryption (and hence security) in the hands of server rather than leaving it to the clients. In absence of these settings, the client may choose to interact with lower TLS version or choose to go with weaker cipher algorithms. Thus posing the risk of exposing the traffic to malicious users on the network. So, even though the connection would be HTTPS, it would still not be fully secure because of weaker encryption protocol and weaker algorithm usage.
After Configuration
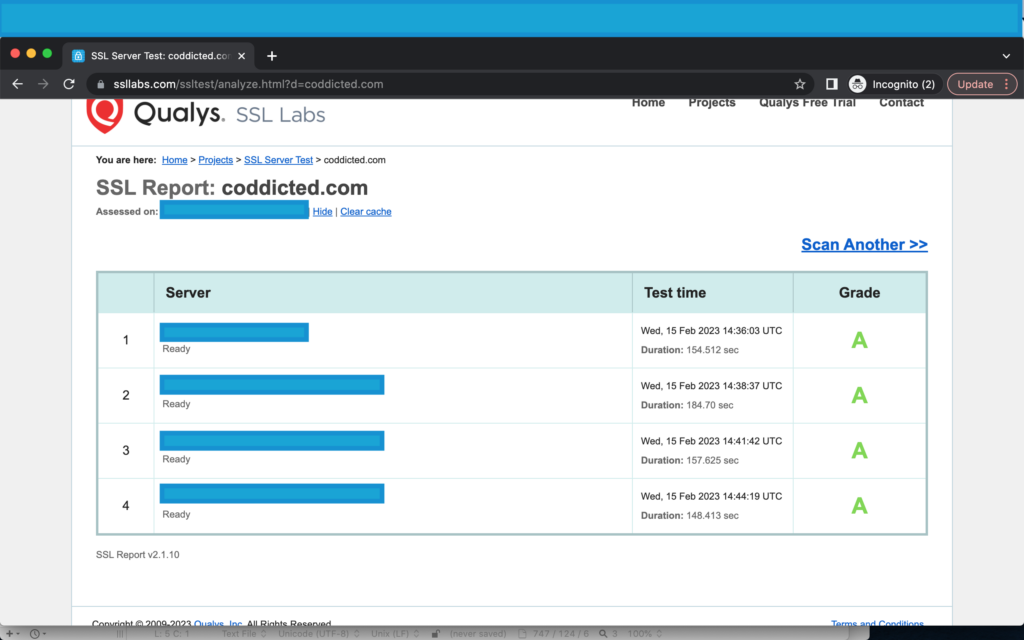
After above configurations, rerun the SSL-Labs test and the results should be ‘up’graded to ‘A‘ grade now.